About this series
In 2023, the cybersecurity landscape changed in three significant ways. The Securities and Exchange Commission cut the allowed reporting period following a security breach to just four days. Artificial intelligence began to be used in cyberattacks. And after retreating in 2022, ransomware came back stronger than ever.
In response to these threats, cybersecurity buyers, vendors, influencers and decision makers worked to improve their practices around ransomware prevention, privacy and third-party risk, vulnerability management, cloud security, and identity and access management. Yet respondents in several CyberRisk Alliance Business Intelligence surveys reported more than a few challenges in meeting these goals.
The following is the fourth of a five-part series about how security practitioners struggled or, in some cases, made significant headway throughout 2023. Here, we focus on how the skills gap between attackers and defenders affected cloud security, and how AI might change the game in 2024.
***
In 2023, adversaries attacked cloud assets and used the cloud for their own nefarious purposes, sometimes doing both at once.
January began with a report that threat actors had been developing cloud skills more rapidly than the legitimate enterprises they targeted, and another that the number of cloud apps delivering malware had tripled in the previous year.
That observation was quickly borne out in April, as the Legion malware hijacked misconfigured cloud-based email servers, then attacked the Amazon Web Services monitoring tool AWS CloudWatch. Another group, TeamTNT, deployed a worm to go after Docker containers, first on AWS but then on Google Cloud Platform and Microsoft Azure as well.
An unnamed threat actor chained together Salesforce and Facebook flaws to pump out phishing emails. A cloud-based command-and-control provider called Cloudzy hosted instances for known criminal gangs and several state-sponsored APT groups, even those from rival countries like India and Pakistan.
Some of Cloudzy's customers were North Koreans, who needed no assistance in launching the supply-chain attack on JumpCloud, likely with the aim of hitting JumpCloud’s cryptocurrency-using clients. Pyongyang's notorious Lazarus Group was also spotted midyear hijacking cloud-based Microsoft IIS servers to spread malware.
All this made the incident in which an attacker hijacked an abandoned AWS S3 bucket to spew malware seem almost quaint by comparison.
Old-fashioned cloud security problems didn't go away, of course. Salesforce and a dating app both spilled sensitive data due to cloud misconfigurations, and ServiceNow was just lucky that its own misconfiguration went unexploited.
Organizations lost track of or just plain forgot about cloud assets, including in Salesforce communities and Azure Active Directory. It perhaps shouldn't have been surprising that 30% of 13 billion files stored in the public cloud were found to contain personally identifiable information.
Lost in the fog
Put together the cloud-related skills and knowledge gap between attackers and defenders with the advent of AI-driven attacks, and we might see a perfect storm of cloud-based and cloud-targeting threats in 2024.
Threat actors might use AI to rapidly catalogue an organization’s cloud assets and probe them for weaknesses, gaining visibility that the targeted organization lacks. Defenders of cloud assets may have to adopt AI-driven monitoring and response tools just to keep up.
An August 2023 CRA Business Intelligence survey of 200 IT and security managers in North America found that cloud adoption was widespread, with 43% of respondents saying that their organizations had moved at least half their workloads into the cloud. Forty-eight percent said they used three or more cloud providers. Only 1% said they didn't use the cloud at all.
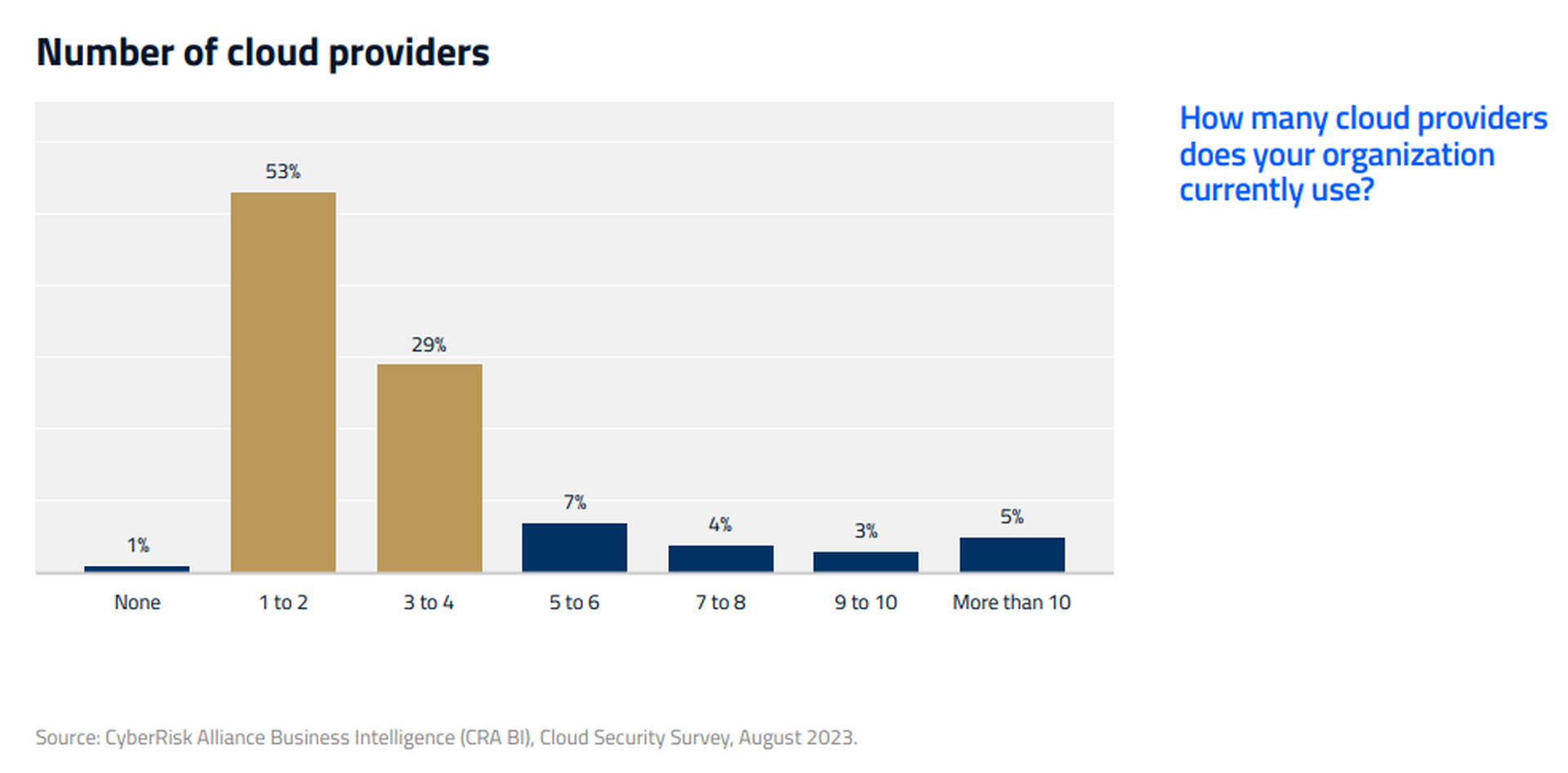
Respondents generally felt comfortable with the security of their cloud platforms, with 56% of respondents rating their confidence levels at 7 or more on a scale of 1 to 10. Two-thirds (66%) said they used the security services offered by their cloud platform providers. Despite that, 22% of Amazon Web Services and Microsoft Azure customers each said their platforms had been compromised in the previous 12 months.
A sizeable fraction of survey respondents had doubts about their own abilities to manage, secure and gain visibility into their own cloud assets.
One-quarter (25%) said they lacked the skills or expertise to properly secure the cloud, 14% said they didn't have the staff to manage the cloud, 13% said they lacked the required experience and 8% said they lacked visibility. Fifteen percent feared they wouldn't be able to handle adversarial attacks on their cloud assets, and 10% felt they needed more resources to manage the cloud.

"We're struggling to understand the complexity that the cloud can introduce and have trouble training and maintaining employees that can stay current with the latest cloud technologies," said one respondent.
Such lack of confidence in organizations’ abilities to manage, track and protect cloud assets doesn’t bode well for compliance with the SEC’s new breach-notification rules. Publicly traded companies may have to devote more resources to improving cloud visibility and security, and to create new procedures and templates that would speed up incident reporting.
2024 to-do list:
Includes guidance from the Cybersecurity Collaborative’s Task Force on vulnerability management.
- Prioritize additional cloud training for IT and security personnel.
- Make sure new or recently added cloud-management tools include AI/ML, especially for asset inventory and misconfiguration and vulnerability detection.
- Develop rapid cloud-breach reporting procedures to comply with SEC rules.




