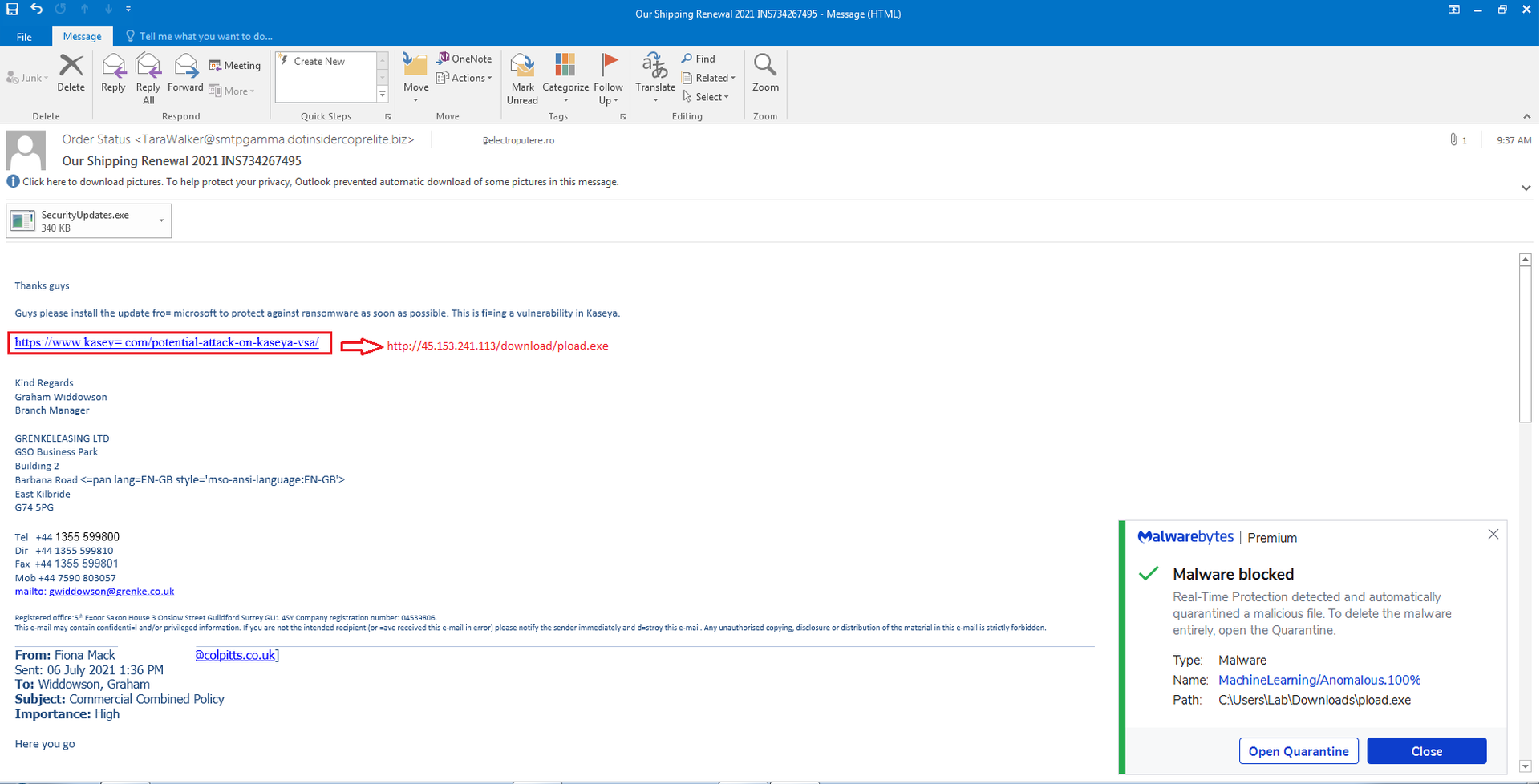
Malwarebytes detected a phishing campaign taking advantage of Kaseya VSA customers eagerly awaiting a patch for the beleaguered remote monitoring and management application.
The company tweeted Tuesday night that it had caught malicious spam claiming to both contain and link to a Microsoft tool to "protect against ransomware" on a visually similar domain to Kaseya. The executable, titled "SecurityUpdates.EXE", instead dropped CobaltStrike.
While there are several easy-to-identify indicators that the email is fake, starting with the name in the 'from' line not matching the signature, fears stemming from an outbreak of REvil ransomware among on-premises VSA customers are very real and could spur some to be less vigilant.
Click here for the latest news about the Kaseya cyberattack.
A REvil affiliate leveraged a chain of vulnerabilities to hack at least 50 VSA customers, including several managed service providers, resulting in more than a thousand downstream MSP customers being infected with ransomware.
Kaseya immediately took its SaaS VSA product offline as a precautionary measure after the attack began Friday. It has since announced it would restore SaaS before releasing a patch to the on-premises product and is currently testing the SaaS restoration.
"During the deployment of the VSA [SaaS)]update an issue was discovered that has blocked the release. We have not yet been able to resolve the issue. The R&D and operations teams worked through the night and will continue to work until we have unblocked the release. We will provide a status update at 12:00PM US EDT," Kayesa wrote on its blog.
The Cybersecurity and Infrastructure Security Agency is expected to release guidance for customers returning to the SaaS product timed with the release.
The event has received widespread attention due to a global pool of victims, feeding into an environment ripe for phishing exploitation. President Joe Biden and Vice President Kamala Harris will meet with leaders across the administration to discuss ransomware Wednesday morning, including representatives from the departments of State and Homeland Security.