| Product: ImmuniWeb Discovery | Category: Attack Surface Management |
| Company: ImmuniWeb | Review date: April 2021 |

This review is part of the April 2021 assessment of the Attack Surface Management (ASM) product category. If you haven’t read the category overview, you might want to check it out – it explains the category’s basics, use cases and the general value proposition. Our testing methodology explains both how we interact with vendors and how we tested these products. In short, ASM products aim to discover and manage an organization’s external digital assets. This approach extends far beyond assets with an IP address, however, including everything from certificates to S3 buckets to DNS misconfigurations.
Company background
An application penetration tester by trade, Ilia Kolochenko founded his first cybersecurity consulting firm named High-Tech Bridge in 2007. Later, he saw an opportunity to build a product focused on automating large portions of the penetration test. Ilia successfully exited High-Tech Bridge and launched ImmuniWeb in 2019 with Kolochenko as the CEO and Chief Architect.
The company is headquartered in Geneva, with its staff of 50 partially remote, spread across Europe and the United States.
Product summary
ImmuniWeb occupies an interesting space in the ASM market. While it offers many features only seen in some of the more complex ASM offerings, pricing is SMB-friendly and getting started with the product requires nothing more than a credit card.
ImmuniWeb offers product offerings and subscription packages too numerous to go into here, but clearly laid out on the website. The product this review will be focused on is the Corporate Pro subscription for ImmuniWeb Discovery, which combines attack surface monitoring with data leak discovery.
Target market: While ideal for small-to-mid-sized enterprises or one-off projects (e.g. M&A due diligence), ImmuniWeb states that 90% of customers are actually mid-to-large-sized enterprises, including a large European telco.
Time-to-value: ImmuniWeb requires a lead time of 3-4 days to prepare an initial dashboard. We found ImmuniWeb’s results remarkably free of noise. It took a few hours to browse through the initial results.
Maintaining value: For a mid-sized enterprise (hundreds, not thousands of exposed assets), expect to spend 1-2 hours per week reviewing new findings as they come in. This is ideal work for a junior analyst or as a shared role between DevOps engineers.
Total cost: The Corporate Pro subscription is $11,940 USD annually. In a mid-sized enterprise (100-2,000 employees), we’ve estimated two hours of analyst time to do the initial analysis. Based on our average salary estimates, this labor totals $100.96. For ongoing analysis work, we’ve estimated two hours of junior analyst time per week, which totals $3499.60 per year. The total annual cost to use this product comes to $15,540.56.
Strengths: As flexible to purchase as it is to use. In addition to perpetual use, it is also designed for single use cases, such as a one-off consulting engagement, or M&A due diligence.
Weaknesses: What will make the ImmuniWeb interface great for some, might not work as well for others. Asset information tends to get bundled into logical groups. This will work well for smaller shops or anyone with less time to spend on ASM. However, some may prefer their assets broken out, with things like software components and DNS names in searchable, filterable lists.
Conclusion: Makes big dollar features available to the little guys.
Deployment and configuration
Creating an initial Discovery project requires only a company name and a credit card. In a few days, the dashboard will be ready and populated. There are few settings to worry about, but it’s worth noting that ImmuniWeb does support 2FA in the form of SMS or Email based one-time passcodes.
Usage
The ImmuniWeb interface, with all its bold primary colors, is downright cheerful. We’re not sure even the most curmudgeonly hacker could hate the clean interface, crisp UI elements and intuitive data visualizations.
Findings are spread across six categories: Web, Mobile, Cloud, Network, Code Repositories and Incidents that include Dark Web exposures. Each section is arranged with dashboard widgets (charts showing data summaries and trends, mostly) at the top, with detailed lists of findings underneath.

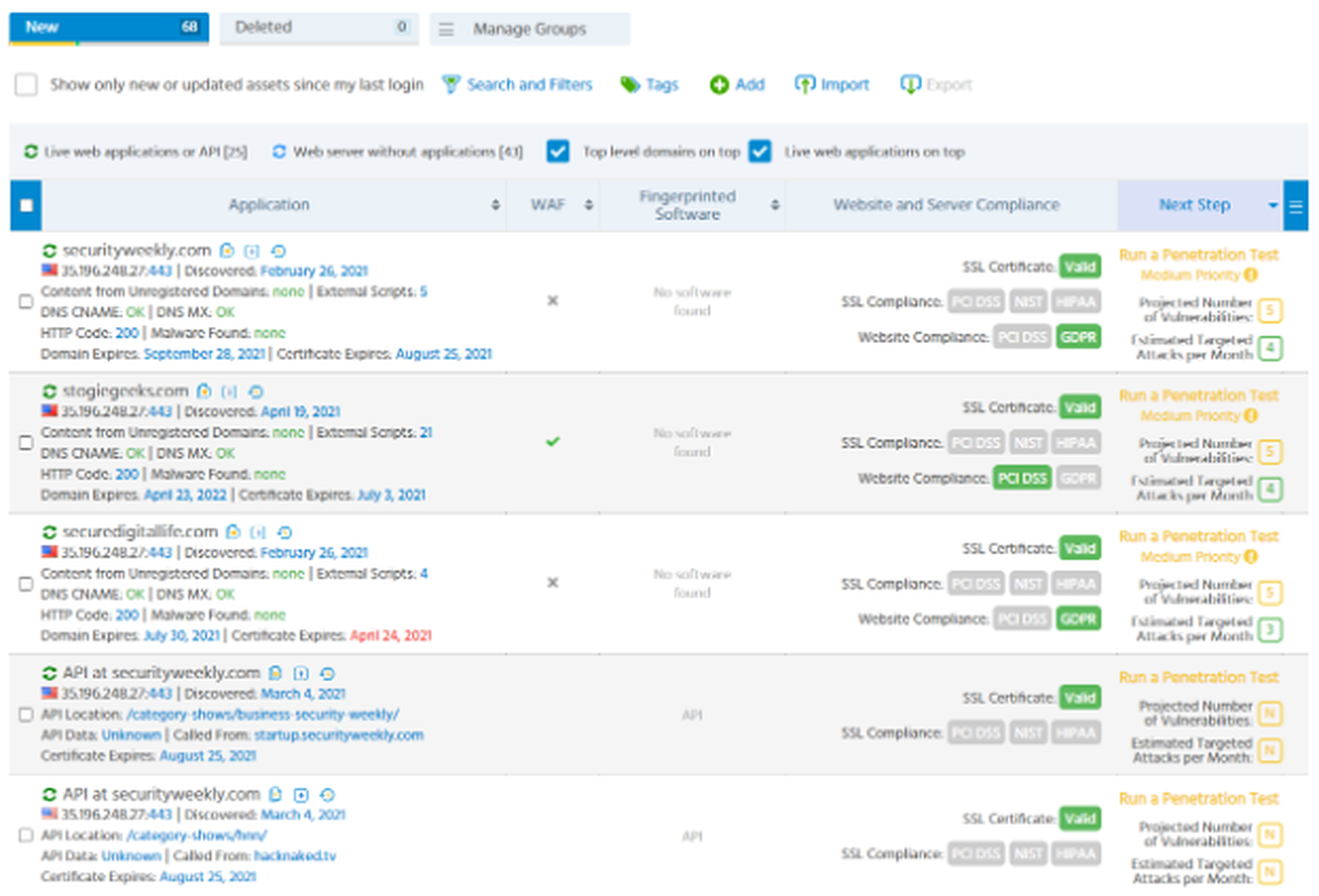
You’d be forgiven for needing a moment to take in all the data available on this screen. Though it’s a lot of data, it somehow remains easy to consume and navigate. The all important ability to search and filter is present, with plenty of options to hone in on very specific criteria. We also like the addition of ‘suggested’ filters, like “Assets that failed PCI DSS compliance” and “Assets with DNS misconfigurations”.
From this screen it is possible to add tags and add additional assets. The ability to schedule an on-demand penetration test on a particular asset is also notable, along with a prediction of the vulnerabilities that will be found by the pen test.
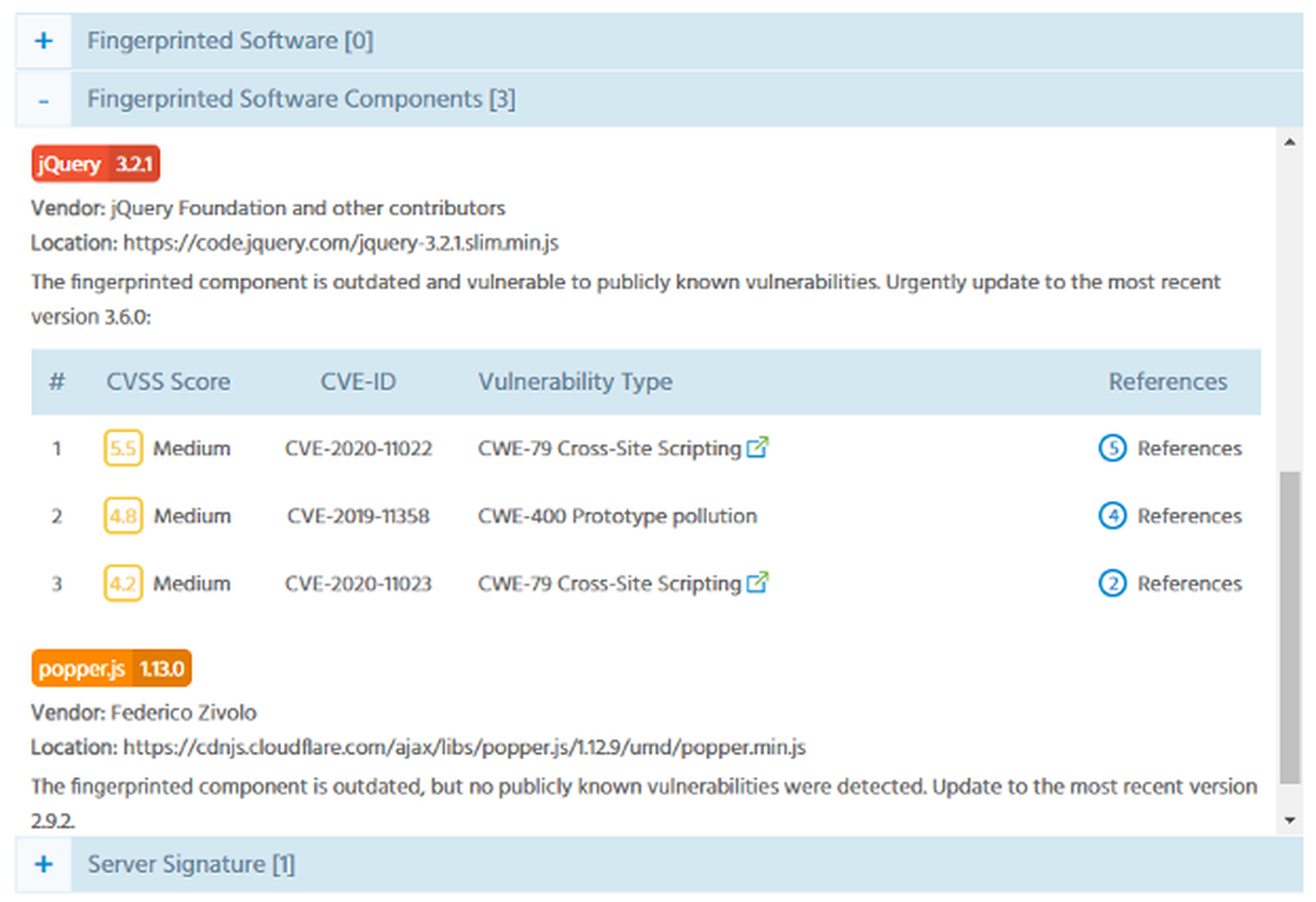
Generally, throughout this interface, any element with a color that corresponds to a severity level will open up more details about a discovered issue or vulnerability. These details include things like CVSS scores, CVE-IDs, CWE mapping and links to vulnerability references.
Moving on from the Web tab, the mobile tab shows any mobile apps related to the company, across both first party and third party (largely unsanctioned) app stores – a unique feature across all the ASM products we reviewed. Any apps discovered are automatically scanned for issues. As with web applications, there’s also an option to launch an ad-hoc mobile app penetration test.
The cloud tab digs into third party infrastructure hosting company assets. CDNs, SaaS vanity URLs, hosting infrastructure and even newsletter platforms and Slack instances were discovered in our testing.
The Network tab lists IP addresses and common open ports, with an option to perform full port scans on each asset. Throughout each of these tags, assets are assigned estimated risk scores and prioritized by default.
The Code Repository tab was an interesting one. Many open source projects have linked to Security Weekly articles and podcast recordings over the years. Some of these projects have been forked many times, making this section the most difficult to sort through, with more than double the findings of the next closest category. It’s highly possible that we’re an exception from the norm here.
It wouldn’t be accurate to call these false positives, however. All these repositories are legitimately linking to our assets, which is worth being aware of.
Finally, the Incidents tab is focused on data leaks from many different sources, ranging from dark web marketplaces to paste sites to known compromised credentials. Potential cases of domain squatting are also listed here. We plan to do a separate group test on data leak discovery tools, so we won’t dig too deeply into the Incidents tab here.
When it comes to reporting, the notification options are incredibly granular. It’s possible to set different frequencies for nearly every type of asset discovery. By default, everything is set to send weekly notification emails. A well-documented API gives programmatic access to all the data featured across the six asset categories we’ve explored.
Support
24/7 support is available via ticket creation within the product. It’s possible to view the status of current tickets or open new ones from within the ImmuniWeb app.
Claims
ImmuniWeb claims its proprietary AI technology can save as much as 90% on human labor. As part of this group test, we performed a baseline assessment using common active and passive reconnaissance tools. We can’t attest to how much credit AI gets, but if anything, a 90% time saving estimate is conservative.
ImmuniWeb also claims to “…Simplify, Accelerate and Reduce Costs of Application Security Testing, Protection and Compliance”. This is a perfectly reasonable claim. In fact, we didn’t really find any unreasonable claims in ImmuniWeb’s marketing.
Security program fit
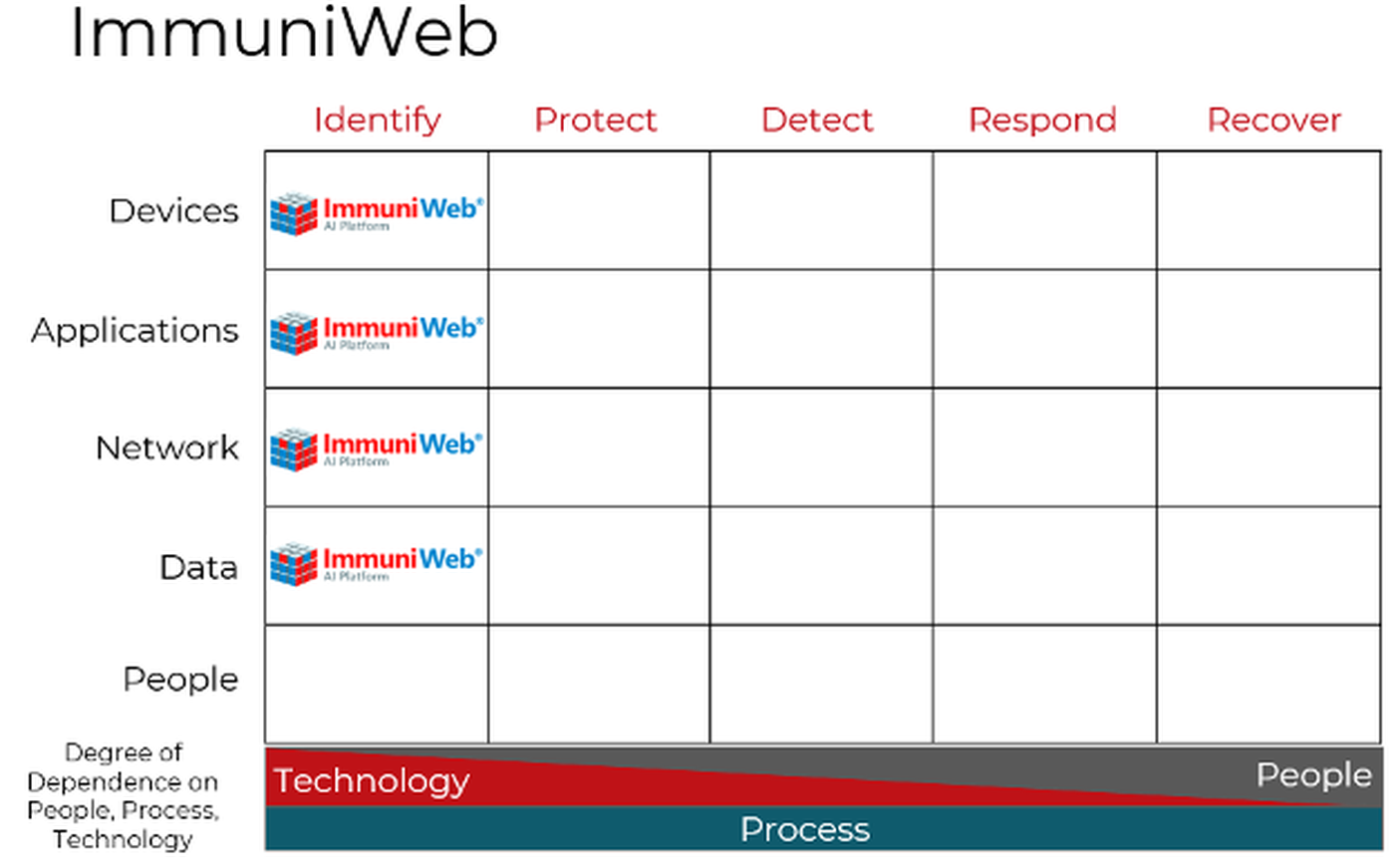
Like other products focused on discovering vulnerabilities and misconfigurations, ImmuniWeb fits solidly within the Identify column of the Cyber Defense Matrix. The products’ data leak discovery features land it in the Identify Data space in addition to Devices, Applications and Network.
Conclusion
ImmuniWeb Discovery is an impressively comprehensive offering for the price. The low false positive rate and the pricing flexibility make it easy to reach for in a number of situations. The reach into data loss detection and the inclusion of mobile app discovery potentially save buyers additional time and money.



