To grow your business, your organization must scale its cybersecurity program. It will need to comply with multiple frameworks and regulations along the way. This isn't always easy. Layers of compliance requirements introduce complexity, which increases the risk of you wasting time and money as you try to fulfill your objectives one at a time.
Fortunately, you can minimize waste and scale your cybersecurity program more efficiently by planning out your compliance objectives. You can do this using proven security best practices that map to or are referenced by industry regulations and frameworks.
Security fundamentals for streamlined compliance
Your compliance requirements vary, but they probably overlap in terms of their security focus. To avoid duplicate effort, you can use two sets of security best practices developed by the Center for Internet Security® (CIS®): the CIS Critical Security Controls® (CIS Controls®) and the CIS Benchmarks™.
Improving your cybersecurity posture with the CIS controls
The CIS Controls are a prescriptive, prioritized, and simplified set of security measures for defending against common cyber attack vectors. Developed using a unique community consensus process, the Controls tell you the actions you need to prioritize to become more secure. This prioritization helps your organization lay a foundation of essential cyber hygiene and scale from there rather than trying to navigate your way through a list on your own.
The CIS Controls map to many regulations and frameworks that might be applicable to you. These include:
- Federal Financial Institutions Examination Council (FFIEC-CAT),
- Health Insurance Portability and Accountability Act of 1996 (HIPPA),
- MITRE Enterprise ATT&CK v8.2,
- National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) v2.0,
- Payment Card Industry (PCI) Data Security Standard v4.0,
- And so much more!
With your compliance objectives in mind, you can set a course to manage your prioritization and implementation of the Controls. The pro version of the CIS Controls Self Assessment Tool (CIS CSAT) enables your security teams to create an implementation plan and assign individual tasks. They can then use that plan to track and verify the assignment, implementation, automation, documentation, and reporting of specific Controls and CIS Safeguards — insight which can drive your efforts to fulfill your compliance objectives and scale your organization's cybersecurity program.
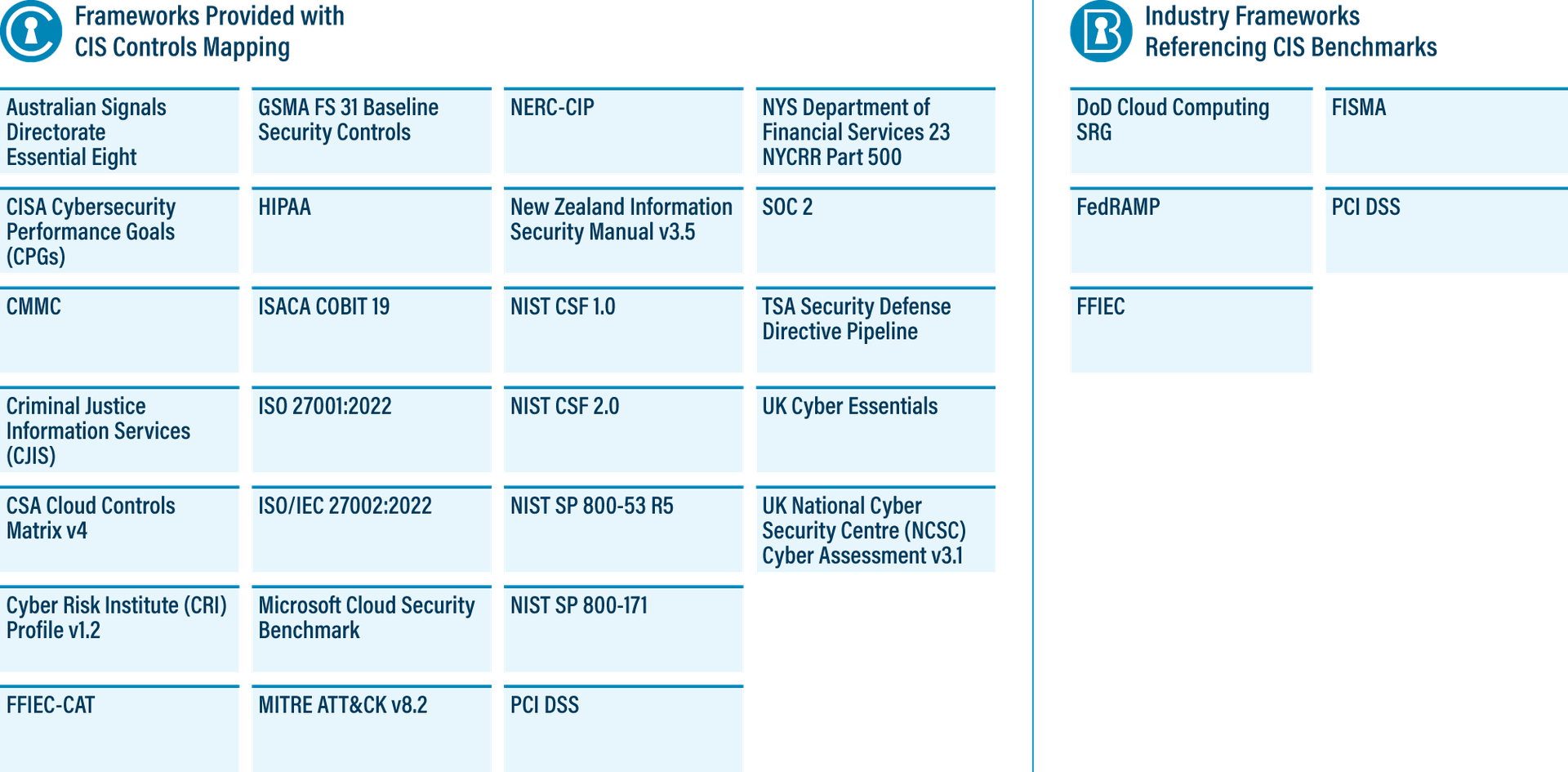
CIS Benchmarks’ Secure Recommendations Referenced in Industry Standards
CIS Control 4 focuses on secure configurations, which is where the CIS Benchmarks come in. They provide consensus-based guidance for 100+ technologies across more than 25 product vendor families.
The secure recommendations of the Benchmarks help you strengthen your cybersecurity posture, as each Benchmark maps to the Controls. Additionally, multiple industry regulations reference the Benchmarks as a standard for protecting the following types of information:
- Financial — PCI DSS specifically mentions the Benchmarks as a means of hardening.
- Government — The Department of Defense (DoD) Cloud Computing Security Requirements Guide names the Benchmarks as an alternative to other resources, such as the Security Technical Implementation Guides (STIGs) and Security Requirements Guides (SRGs).
- Medical — The Benchmarks overlap with and therefore complement the HIPAA security rule.
- Cloud-based products and services — FedRAMP suggests you use the Benchmarks in the event you can't for a certain platform.
To determine if you've securely configured your systems, you can use a configuration assessment. CIS-CAT® Pro, specifically its Assessor component, allows you to do just that by comparing the conformance of your systems' settings to the secure recommendations of the Benchmarks. CIS-CAT Pro also comes with a Dashboard component you can use to track your conformance (and hence compliance) efforts over a recent period of time.
Scale your compliance efforts with a CIS SecureSuite membership
The Controls and Benchmarks enable you to manage your secure configurations and scale your cybersecurity program all while streamlining your compliance efforts. To make an even greater impact and obtain access to tools like CIS CSAT Pro and CIS-CAT Pro, you can purchase a CIS SecureSuite® Membership. It is a cost-effective way for you to strategically fulfill your compliance needs and scale your cybersecurity efforts over the long-term.
Interested?




