After a downturn in attacks and payouts in the previous year, ransomware roared back in 2023, with a near-record haul of $450 million midway through the year and an all-time monthly high of 514 reported incidents in September.
[Editor's Note: The following is an excerpt from the report "2023 Cybersecurity Year in Review" - a comprehensive look back at major cybersecurity events of 2023 that will shape the year ahead.. DOWNLOAD your FREE PDF copy of the report here.]
The highest-profile ransomware incident was the September attack on MGM Resorts, which reportedly encrypted more than 100 hypervisors and forced the company to shut down its nationwide computer network, incurring an estimated $100 million loss.
The same attackers, the Scattered Spider group, also hit rival gaming giant Caesars Entertainment, which chose to pay a $15 million ransom rather than suffer through costly disruptions. As of mid-November, the FBI was catching heat for not making any arrests in the cases despite apparently knowing the identities of the attackers, who seemed to be mostly English speakers living in Western countries.
A trend that had a greater impact was the continuous onslaught upon health-care providers, who had no respite from ransomware attacks. Attackers became even crueler than before in 2023, hitting cancer centers, threatening to release patient information, knocking the Prospect Medical Holdings hospital system offline nationwide and hitting 30 hospitals across six states over the long Thanksgiving weekend.
To cap it off, a new report found evidence for what health-care providers have long feared: Ransomware attacks slow the pace of patient treatment and lead to hospital overcrowding, increasing risks for patients who need immediate treatment for such time-sensitive emergencies as strokes and heart attacks.
New confidence in combatting ransomware
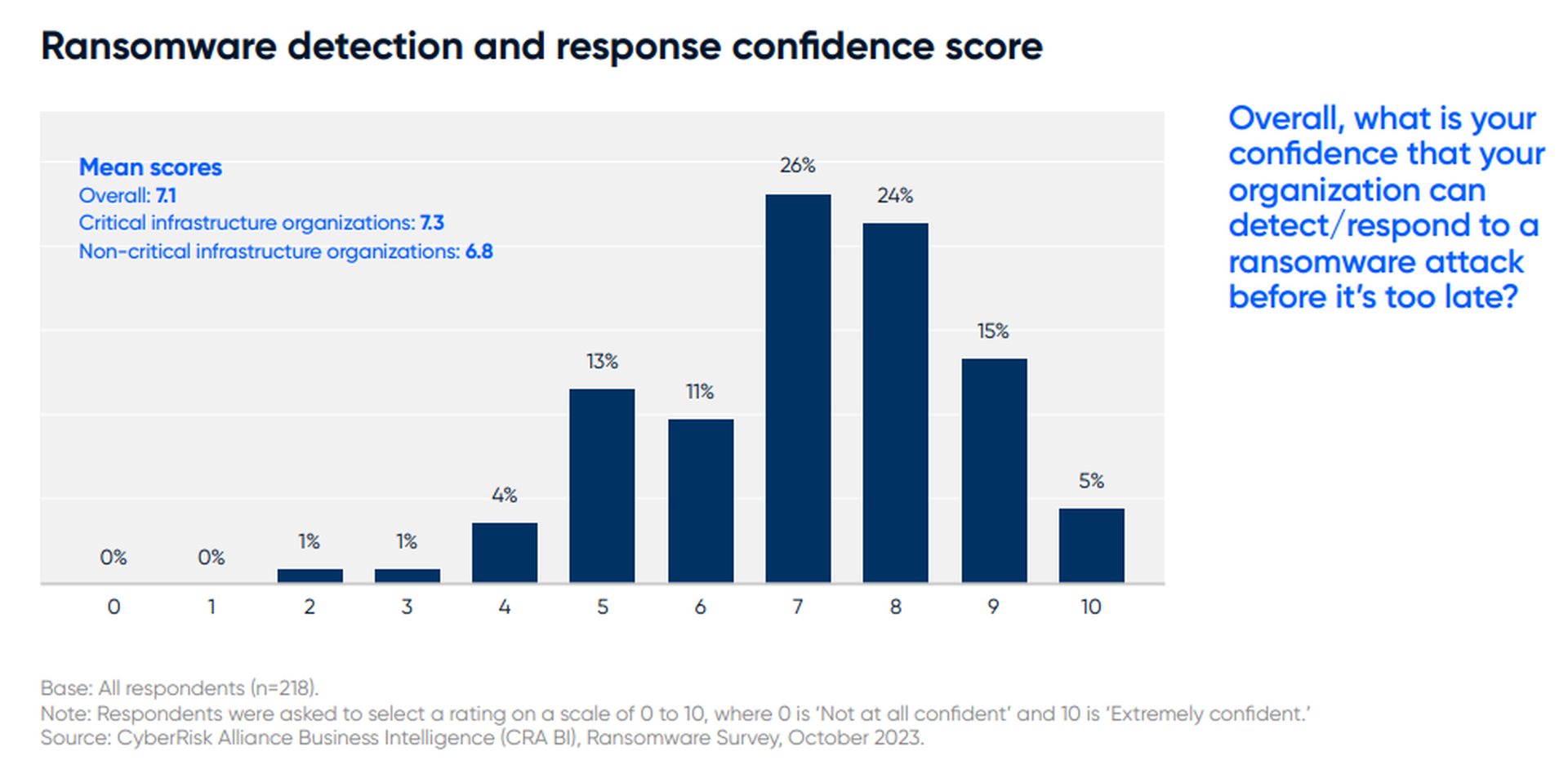
An October 2023 CyberRisk Alliance Business Intelligence survey of 218 North American security and IT leaders found that 19% had suffered a ransomware attack on their organizations within the previous 24 months. However, none said they had paid the ransoms. A third of the non-payers said backups saved their data, 24% said the lost data wasn't important, and another 24% said they resolved the issues on their own.
Overall, organizations seemed to be growing more confident that they could successfully respond to ransomware attacks. Seventy percent of survey respondents had "moderate to high levels of confidence" in their companies' abilities to handle ransomware attacks, and 79% said they had mostly or fully completed secure backups of critical data.
"We implemented ransomware protection tools from third-party vendors, and we have a dedicated team to monitor threats regularly," said one survey respondent. "Our confidence level is high based on the precautionary measures we take."
Weekly backups, cloud deployment and strong executive support were what let an Ohio bottling company recover from a ransomware attack in only seven hours, its security chief told a Cybersecurity Collaboration Forum CyberRisk Leadership Exchange conference in Cincinnati in June 2023.
"We never missed an order. We never missed a delivery. Customer data was not compromised," said Brian Balzer, Executive VP of Digital Technology & Business Transformation at G&J Pepsi-Cola Drink Bottlers, Inc. "I'd say probably 95% of the organization had no idea that we were under attack."
The game may be about to change
Such confidence may be essential when the SEC’s new four-day reporting rule goes into effect. Publicly traded companies will need to prepare incident-response strategies and templates that enable quick information-gathering and report generation to meet the SEC deadline.
Unfortunately, organizations in sectors hit hardest by ransomware, such as healthcare and education, often have ineffective security safeguards. Few educational institutions are public companies, but we may see a record number of breach-related SEC penalties levied against publicly traded healthcare providers in 2024.
Rapid developments in AI may also shift the high ground back to attackers. In the CRA survey, fully 66% of respondents listed AI aiding attackers as one of their top five ransomware concerns. When asked specifically about AI, 83% were moderately or very concerned that AI might enhance ransomware attacks, although 71% thought that AI might help defend systems, too.

2024 to-do list:
- Develop a plan for AI’s impact on ransomware, including both how to counter AI-assisted attacks and how to incorporate AI into your defenses.
- Develop rapid-response procedures to enable quick SEC reporting following a ransomware incident.
- Healthcare organizations should put more resources toward cybersecurity.
- Educational institutions should take advantage of cybersecurity-improvement programs such as the U.S. Department of Education’s K-12 Digital Infrastructure Brief and free offerings from Amazon, Cloudflare and Google.
About this series
In 2023, the cybersecurity landscape changed in three significant ways. The Securities and Exchange Commission cut the allowed reporting period following a security breach to just four days. Artificial intelligence began to be used in cyberattacks. And after retreating in 2022, ransomware came back stronger than ever.
In response to these threats, cybersecurity buyers, vendors, influencers and decision makers worked to improve their practices around ransomware prevention, privacy and third-party risk, vulnerability management, cloud security, and identity and access management. Yet respondents in several CyberRisk Alliance Business Intelligence surveys reported more than a few challenges in meeting these goals.
The following is the first of a five-part series about how security practitioners struggled or, in some cases, made significant headway throughout 2023. Here, we focus on the gains and losses in the battle against ransomware, and why the threat landscape and compliance obligations may soon change.